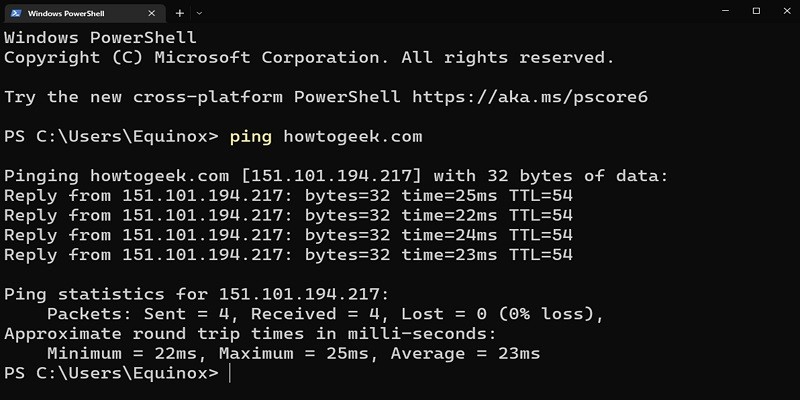
How To Ping A Website In Windows?
To ping a website in Windows, open the Command Prompt by pressing the Windows key + R on your keyboard and typing “cmd”. Then type in the command “ping” followed by the URL of the website you want to test. The command should look like this: “ping www.examplewebsite.com”. Press Enter to run the command and […]
Continue Reading